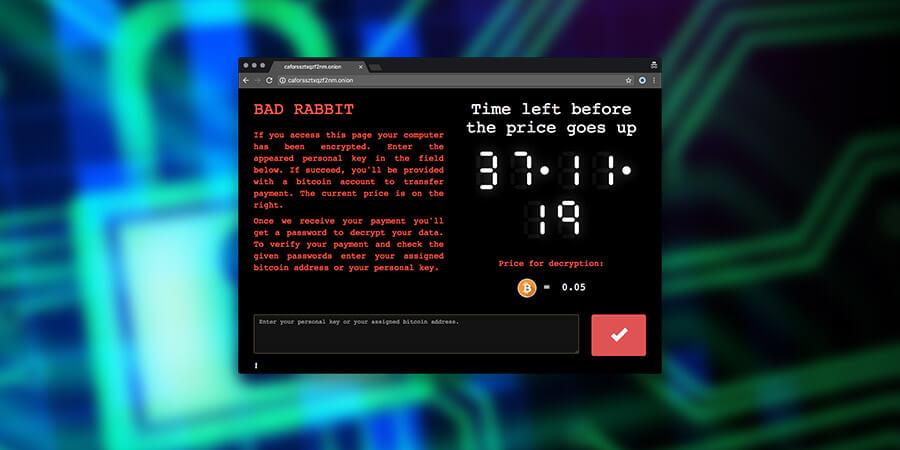
Russia, Ukraine, and other areas have been hit by a new strain of ransomware called ‘Bad Rabbit'. The ransomware is said to bear similarities to the WannaCry and Petya outbreaks that caused chaos earlier this year. According to reports, it's unknown how far this new malware will spread.
US officials said "multiple reports of Bad Rabbit ransomware infections" had been reported "in many countries around the world". The US computer emergency team said it "discourages individuals and organizations from paying the ransom, as this does not guarantee that access will be restored."
Russian news agency Interfax was affected by the ransomware and also Fontanka.ru. Ilya Sachkov, head of Russian cybersecurity firm Group-IB, said, "In some companies, the work has been completely paralyzed – servers and workstations are encrypted." Most of the victims were located in Russia, according to Kaspersky Lab, and a few cases in Turkey and Germany.
Victims of the ransomware had their computer contents encrypted. The hackers asked for a payment to release the data – in this case 0.05 bitcoins which is about $280. It was only a matter of time before a new strain of ransomware came along, said Gregg Petersen from software firm Veeam. The attack appeared to be targeted at corporate networks.
"We continue to see this lucrative business of ransomware wreak havoc, as the perfect storm of poor maintenance of updates, weak security measures, employee and user errors of judgment, and pseudonymous crypto-currencies exist," Petersen said.
Most anti-virus programs aren't able to detect the ransomware, according to analysis by virus checking site Virus Total. The malware was distributed via a bogus Adobe Flash update, claims security firm Eset. The malware's code, according to a screenshot posted by researcher Kevin Beaumont, referenced pop culture characters including the names of two dragons from Game of Thrones.
To prevent further attacks, Petersen suggests that updates should be maintained, processes to support IT securities policies should be adhered to, and robust IT defenses should be put in place. Organizations should also have backup data located off the live IT network, he said, which should be "a key part of your data management strategy."