As major network operators around the world launch new 5G services, the topic of 5G security risks emerges and the security of telecom networks, in general, becomes the focus of government agendas and regulatory agencies.
The broad scope of 5G use cases allows the network to become an increasingly attractive target for cybercriminals. The available threat surface has expanded along with the consequences of any possible damage that can be inflicted.
While the 5G deployment race continues, it is a must that one of the most important networks within the industry 4.0 era is sufficiently secure to maximize its technological prowess. Fast implementation is indeed important, especially in the increased demand for connectivity today, but security remains the priority.
Fifth-generation networks involve the user (device and applications), companies (operators and vendors), and authorities as well who are aware of the vulnerabilities that this technology entails. Let us look at the various efforts being done to make 5G security robust and how these could guarantee safe connectivity in the years to come.
Impact of 5G in cybersecurity
5G networks are claimed to be more vulnerable to cyberattacks than previous generations (2G/3G/4G). They are mainly deployed to deliver enhanced mobile broadband, enable massive machine-type communications, and allow ultra-reliable and low latency communications, thus establishing the right security approach for emerging 5G networks is critical.
In terms of deployment, there are two main categories. Non-standalone (NSA) 5G is available where 5G base stations anchor the control signaling to the 4G core, whereas stand-alone (SA) consists of 5G new radio network (NR) connected to a 5G core network (5GC). Both open up new security challenges for both operators and consumers.
Here are some points of vulnerability brought about by 5G:
- 5G works via distributed, software-defined digital routing instead of centralized, hardware-based switching. In this case, distributed cloud computing makes it possible to create network slices for better resiliency and latency. From a security perspective, the distributed cloud may introduce new attack vectors against the 5G network without any built-in security.
- 5G further complicates its weak spot by virtualizing in software. Different levels of isolation can be considered spanning from a single node of the core network to fully dedicated radio access. 5G network slices require high reliability, resiliency, safety, security, and privacy.
- The fact that the network is being managed by digital software indicates susceptibility by nature. An attacker that gains control of the software managing the networks can also control the overall network. According to GSMA, previous versions of core mobile networks suffered from a misplaced trust model, namely that only those who were entitled to access to the core network were actually provided with access. Hence, 3GPP has specified that all links between 5G core networks must be authenticated.
- There will be 25 billion IoT devices by 2021, as per Gartner. This massive amount of smart devices forming the Internet of Things (IoT) brings more vulnerability that affects 5G networks. As it becomes more widespread, the IoT phenomenon continues to expose more 5G security risks.
These potential security impacts can evolve into major cyber risks if not prevented. With the advent of 5G, organizations must have network security solutions designed for and capable of protecting 5G-connected devices.
5G security features and network infrastructure
5G standards development has adopted secure/private-by-design principles that include new mutual authentication capabilities, enhanced subscriber identity protection, and additional security mechanisms.
Despite being a common solution for other digital services such as online banking, it is a major paradigm shift to existing mobile telecom practices. Accordingly, the 5G security architecture is designed to integrate 4G’s existing security. But, it should be more intensified to handle various security threats such as attacks on radio interfaces, signaling planes, masquerading, bidding down, man-in-the-middle, and inter-operator security issues.
Visibility, inspection, cloud-based threat analytics, security functions integrated with open APIs, and data-driven threat prevention can be included in a comprehensive end-to-end 5G security strategy. Focusing on data integrity, 5G introduces a new network architecture element: the security edge protection proxy (SEPP).
The SEPP is used to protect control plane traffic that is exchanged between different 5G public land mobile networks (PLMN). As such, the SEPP performs message filtering, policing, and topology that ensure end-to-end confidentiality and/or integrity between source and destination network for all 5G interconnect roaming messages.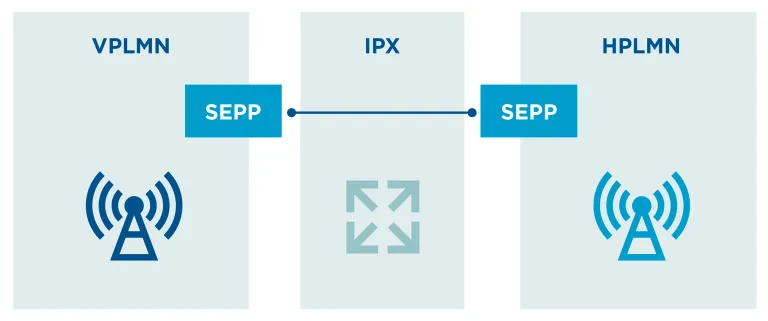
The SEPP is designed to provide application layer security and protect against eavesdropping and replay attacks as well as offer key management mechanisms for setting the required cryptographic keys and performing the security capability negotiation procedures.
5G will require a new transmission infrastructure, including thousands of cell towers and tens of thousands of antennas, known as small cells and distributed antenna systems (DAS). To ensure a high level of protection, user equipment must support a globally unique temporary UE identity (GUTI) that would provide the subscriber identity confidentiality.
The 5G network provider is in charge of subscriber privacy as well as provisioning and updating the home network public key and that key’s identifier. As the user connects to the nearest 5G base stations (gNB), the 5G gNB must support the encryption of user data in transit and for radio resource control (RRC) signaling.
The gNB should activate the user data encryption process based on the set security policy. The encryption algorithms will be used for data confidentiality. Also, in order to fight against international mobile subscriber identity-catcher (IMSI) catchers, 5G introduces the subscriber permanent identifier (SUPI) and a PKI for the encryption of the SUPI into the subscriber concealed identifier (SUCI).
In terms of privacy, Nokia suggests that messages should also be encrypted before it is sent to a location-based service provider. When the quality of location information is reduced (obfuscation techniques), this can protect location privacy as well. Moreover, location cloaking algorithms have also proven effective against timing attacks.
Outlook of 5G security market
The major drivers for the 5G security market include rising security concerns in the 5G networks, increasing ransomware attacks on IoT devices, and rising attacks on critical infrastructure. With this in mind, the 5G security market size is projected to grow at a compound annual growth rate (CAGR) of 44.3%, reaching $5.226 billion by 2026.
In an enterprise’s business environment, services play a vital role in the deployment and integration of 5G security solutions. Services are considered as the backbone of the 5G security, as they are instrumental in network testing, planning and optimization, support and maintenance, and consulting.
Evidently, deploying 5G security solutions and services on the cloud are preferred by organizations as they can avoid spending on hardware, storage, and technical staff. These solutions can utilize either or both private and public clouds, depending on the client’s line of business.
The 5G security solutions need to be robust as they require deployment on multiple levels. These include devices, air interface equipment, cloud RAN infrastructure, and mobile backhaul facilities. Mobile network operators (MNOs) will face challenges in convincing business customers that they are more secure with these 5G security solutions than without them. These should be done while not causing alarm about security holes that could have existed prior to the implementation of 5G security solutions.










